Creating a secure FinTech application is a difficult, time-consuming, and, most importantly, costly task. You can avoid possible challenges if your team has the necessary experience and is aware of FinTech security standards. If it doesn’t, your project can exceed its budget and timeline.
Discover further in our article about the critical cybersecurity policies, tools, and methodologies required to build a highly secure and compliant FinTech platform.
Risks Related to Financial Technology Applications
As previously said, developing a secure FinTech solution is not an easy task. Here are just a few of the FinTech application risks businesses can face.

Cybersecurity vulnerability
One significant drawback of FinTech is its ability to enhance the risk to existing financial institutions: the more systems FinTech links, the more potential breaches for cyber attacks to exploit. Because of the diversity of business types and operational systems, there is no “one size fits all” cybersecurity architecture in FinTech. Hiring professional cyber risk management and secure IT development teams can be beneficial for identifying and preventing high-risk cyberattack vectors.
Fraud and treachery
Fraud and treachery have always been big risks when it comes to money. However, with FinTech, these risks are increased. While technology increases consumer access to financial services, it also makes it easier for unscrupulous people to commit financial crimes. More and more scammers have access to technology and come up with new ways to make easy money.
Digital identities
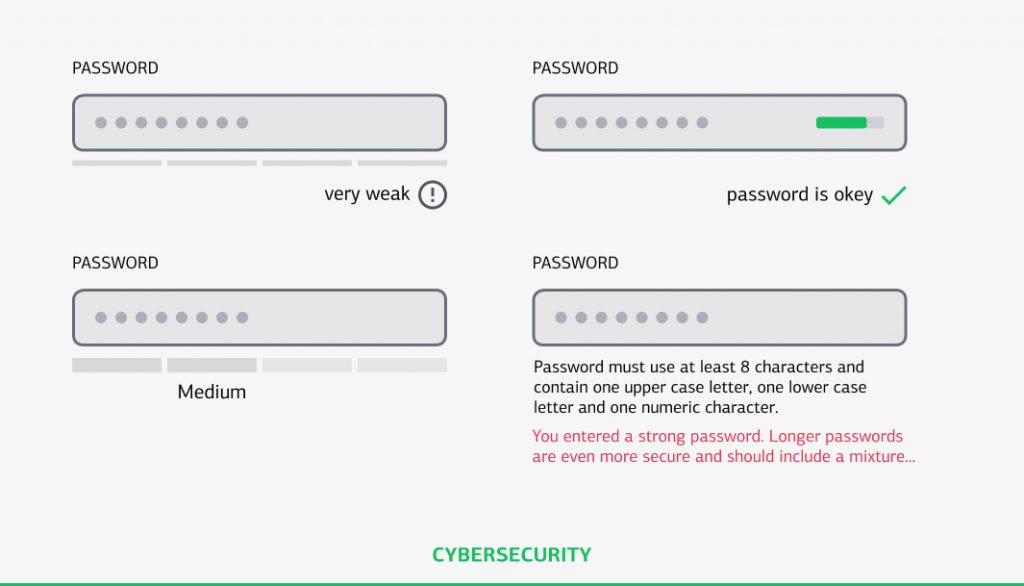
The identification, authorization, and authentication should protect an app from attack or suspicious activity. Even password-based authentication and two-factor authentication (2FA) may be prone to breaches.
FinTech companies require strong strategies and procedures to control who has access to create, modify, and delete their data. Data ownership and responsibility for data require an understanding of several technological and legal processes, as well as compliance with applicable state standards and regulations.
Noncompliance with regulatory requirements
Regulators must guarantee that FinTech companies evaluate risk accurately and apply risk-mitigation practices. Regulators in many countries fall short of keeping up with the rate of technological change. This means that regulatory standards are frequently changing for many FinTech teams, making standardization of compliance processes extremely difficult.

While certain FinTech areas are not as strictly regulated as traditional financial institutions, regulations such as PSD2 and GDPR set particular standards for data protection and system security measures that affect European FinTech sectors in general. National regulators typically impose an additional regulatory layer that impacts FinTechs, such as the CFTC and SEC in the United States, the FCA in the United Kingdom, BaFin in Germany, and ACPR and AMF in France.
Cloud migration
Many FinTech companies have migrated their operations to the cloud to improve performance, scalability, and cost efficiency. However, the complexity and volume of transactions in various cloud settings might make data supervision and protection problematic. The incorporation of yet another technology may introduce new vulnerabilities.
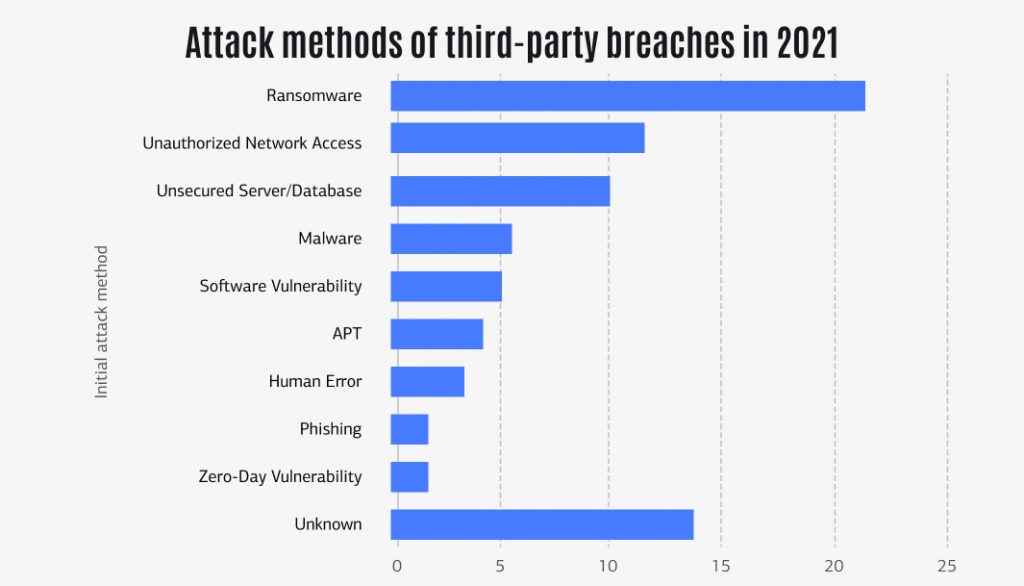
Security breaches in third-party software
The use of third-party software security tools may potentially lead to a security risk. It occurs when FinTechs choose to collaborate with third-party providers to integrate traditional banks, financial security providers, and FinTech startups. This is a dangerous activity since the offered third-party software may be prone to a data breach, which might have negative repercussion consequences: not only do attackers simply access the victim’s online account credentials, steal sensitive data and personal information, and extract huge amounts of money. Your company’s reputation suffers a lot, not to mention the financial damages your company can experience.
Insufficient user transparency
It is not enough for today’s FinTech companies to simply provide more individuals with access to financial services. There should also be an effort to educate people about these services, including what FinTech is, how to use it, and the risks associated with it.
This level of transparency stands in contrast with how banks used to operate, depending on jargon, technical language, and hidden fees to mislead customers and cause them to overspend. However, because FinTech applications are so much simpler to use than traditional channels, there is a higher chance of people using them to avoid terrible consequences.
FinTech Regulations and Policies
The cybersecurity requirements for FinTech app security solutions differ depending on your business’s location and target markets. Let’s take a look at the most frequent guidelines for data protection in the industry of financial services.
GDPR
A set of privacy guidelines for all personal data, including FinTech apps that process information about European Union citizens. GDPR is not restricted to European businesses; if you want to engage with EU residents or businesses, you must comply with this policy.
ISO/IEC 27001
A set of information for all online and FinTech security requirements. It includes procedures and guidelines that can assist businesses all over the world in establishing and maintaining secure data management systems. Cryptography, Access Control, Clear Screen, and Informational Security are among its policies. However, the whole range of essential criteria is determined by the size and location of your company.
PSD2
To assist financial services in securing their technology, the updated Payment Services Directive controls electronic payment services operations in the EU. PSD2 and GDPR frequently overlap and lack legal clarity. As a result, you may need to talk with cybersecurity professionals about this.
eIDAS
Another EU legislation for cross-border electronic transactions is Electronic Identification and Trust Services. Its goal is to offer an universal legal framework for safe transactions amongst FinTech organizations, enterprises, governments, and end users.
APPI
The Act on the Protection of Personal Information applies to financial technology companies who handle private data of Japanese people. This rule, like GDPR, is extraterritorial, which means it applies to corporations that operate from other countries.
PIPA
In South Korea, the Personal Information Protection Legislation provides private data security procedures for both private and public organizations. In contrast to the other FinTech compliance papers on our list, PIPA offenders may face financial penalties as well as criminal prosecution.
FCA
In the United Kingdom, financial services are regulated by the Financial Conduct Authority. This legislation focuses on consumer security and market integrity. Furthermore, local FinTech service providers must go through the FCA registration process.
GPG13
The Good Practice Guide applies to service providers and outsourcing companies working with the UK government system. This compliance guideline is a component of the official Security Policy Framework, which focuses on cybersecurity, event recording, and systems for intrusion detection.
PCI DSS
The Payment Card Industry Data Security Standard applies to organizations that collect, handle, and use credit card data. MasterCard and Visa, for example, require service providers to certify their services to this criteria. The PCI DSS has four levels. The more transactions you execute each year, the more regulations you must follow.
FinTech Security Solutions
Data encryption
Tokenization and encryption are extremely powerful financial security measures. Encryption is the process of encoding data into a code that requires specific keys to decrypt into a readable format. Critical data can be safeguarded using complicated encryption techniques such as:
- RSA is a highly secure asymmetric method that uses both public and private encryption keys.
- Twofish. A freeware technique that divides data into 128-bit blocks for encryption.
- 3DES. The primary way of encrypting credit card PINs. Triple DES splits data into 64-bit blocks that are ciphered three times.
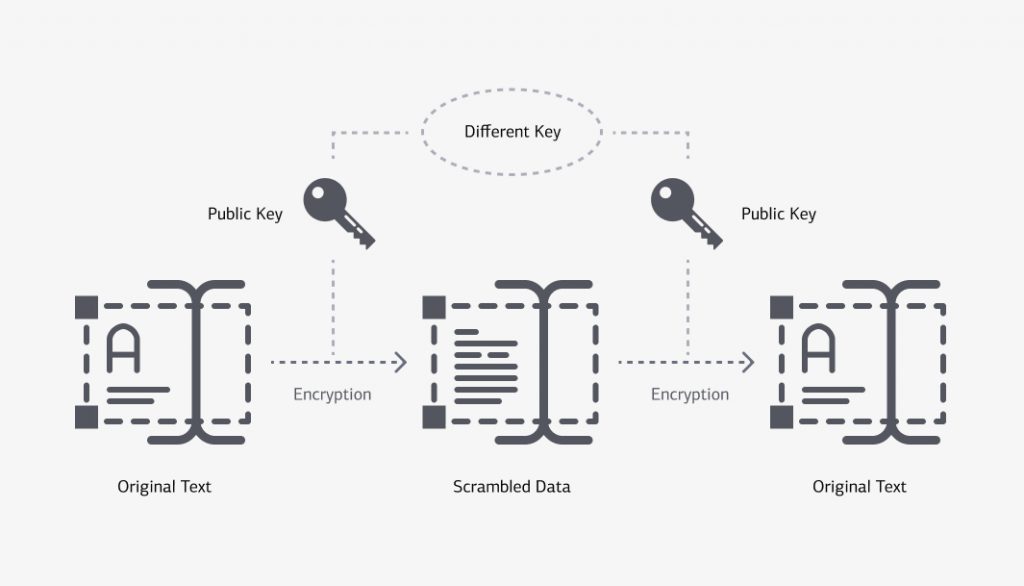
The process of replacing sensitive data with a generated number is known as tokenization (token). Using unique databases, you may decrypt the original information and convert it to a readable version (token vaults).
DevSecOps
Cybersecurity is not a solution. It is a continuous process that should be incorporated into the SDLC (Software Development Life Cycle) when offering fintech development services.
Every day, around 350,000 unauthorized and potential dangerous programs are registered by Internet security agencies. Governmental FinTech policies are also evolving. How can you stay up with the ever changing FinTech cybersecurity landscape?
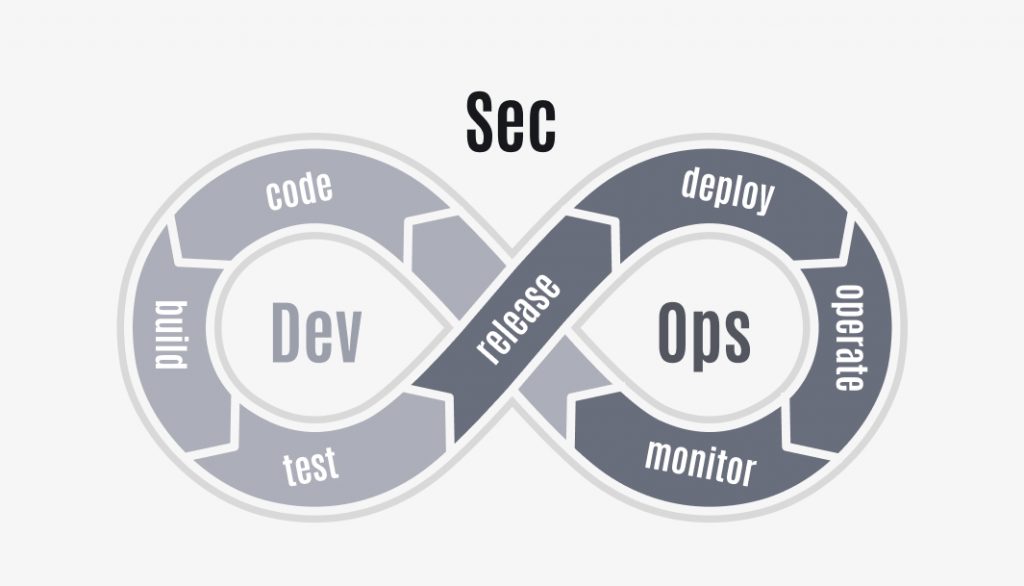
There is a solution. DevSecOps should be used to design secure FinTech solutions. The DevSecOps technique integrates cybersecurity into the production pipeline, encompassing the architectural design, coding, and testing processes.
Secure Access Service Edge
SASE is an all-in-one cloud service. It combines numerous technologies such as software-defined wide-area networking (SD-WAN), firewall as a service, Cloud Security Access Broker, and others.
Secure Access Service Edge provides several advantages, such as enhanced security, easier implementation, bandwidth distribution, and so on. SASE is widely utilized in the FinTech sector because it is easily scalable, allowing it to satisfy the demands of many FinTech customers effectively.
In addition, the SASE architecture monitors network traffic and detects harmful data packets in suspicious transactions, malware, and so on.
Regulatory technology
The regulatory compliance problem for the FinTech business is significant. RegTech, or regulatory technology, is a new trend that uses cutting-edge technology to assist financial institutions in meeting compliance criteria.
RegTech service providers utilize artificial intelligence, machine learning, blockchain technology, and other technologies to assist organizations in understanding regulatory duties, monitoring their material for FinTech security compliance, and so on. Furthermore, RegTech service providers assist businesses with risk management, regulatory management, identity management, data security, transaction management, and other similar functions.
Role-Based access control
RBAC limits network access depending on the user’s relationship to the organization. Your application, for example, may contain the following roles:
- IT expert
- Administrator
- Manager
- Online support services
- Customer
Ordinary employees and end-users will not be able to access company information due to differing access levels. As a consequence, both internal and external security threats will be reduced.
Creating an RBAC-enabled FinTech application necessitates a great amount of knowledge and skill. As a result, you should select a software development company with the appropriate technological stack and background.
Blockchain technology
Blockchain technology is now one of the most important FinTech security trends. Blockchain is classified as a distributed ledger technology because blockchain data is distributed as cryptic hashes among several network nodes rather than being kept on a single computer.
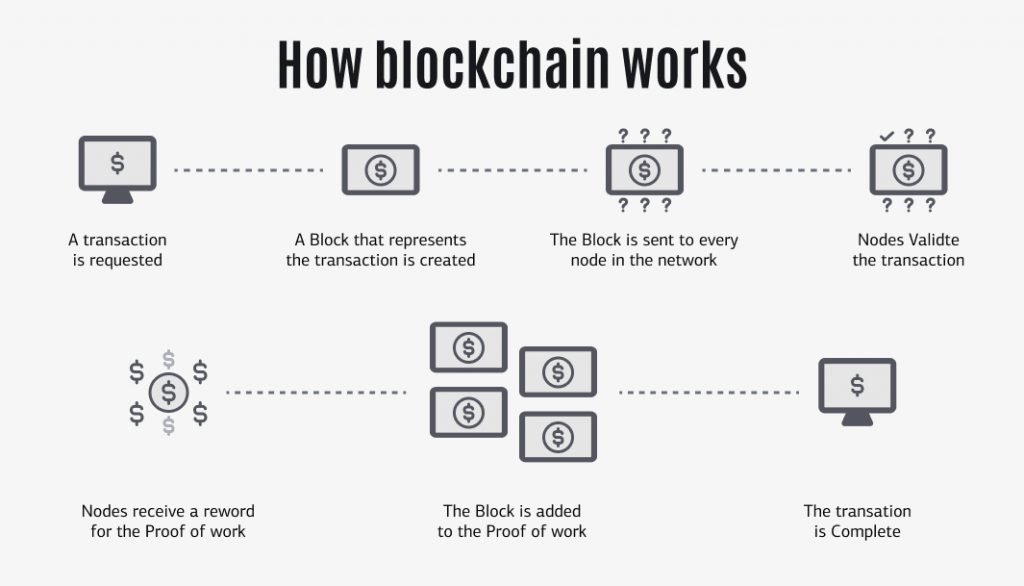
The data is encrypted, and any changes are transmitted via all nodes. This protects the network against data breaches and other suspicious activity by hackers, which would need attacking every practically impossible node.
Neo banking
With the digital change of traditional banking institutions, neo banks are becoming more popular. Neo banks are online financial institutions with no physical locations. Mobile applications allow users to access neo banking services like as online payments, account management, and so on. Neo banking services employ cutting-edge technology such as machine learning and cloud computing to meet consumers’ digital banking needs.
FinTech Security Trends in 2023
Smart contracts
Smart contracts enable parties to sign agreements expressed in computer language using digital signatures, more specifically cryptographic keys. Smart contracts are guaranteed to be precisely and predictably performed.
Because several computing devices receive the identical copy of the original digital contract, the smart contract makes the legitimacy of the contract violation impossible. It’s known as a public blockchain, and it assures the letter’s contract compliance. This FinTech movement is expected to spread across national borders, making smart contracts available to almost anybody.
Apply tokenization
Tokenization is one of the most secure ways to store and transfer sensitive data. It essentially consists of replacing a piece of sensitive information that you need to safeguard, such as a customer’s credit card number, with a newly generated random sequence of symbols (token). Tokens are encryptedly connected to the real data so that the original data cannot be reversed.
Only authorized people are able to decode the original data into a readable format. They must get access to a one-of-a-kind database known as a “token vault,” which keeps all of the relationships between the original data and the produced token.
Encrypt sensitive data
Owners of FinTech apps must secure their data at rest, particularly during transition, when it is easiest to intercept. It is highly suggested that sensitive data be encrypted during transmission.
Encryption uses mathematical procedures to turn data into code that only the intended receiver understands. Without the necessary decryption key, unauthorized users or hackers cannot decipher it. As a result, even if they breach the data, they will not have access to any important information.
Use code obfuscation
Cybercriminals can develop clones of FinTech app security solutions in order to acquire personal information from unsuspecting users. Code obfuscation can be used by FinTech businesses to prevent their apps from copying. Encrypting some or all of the code, stripping out potentially revealing information, labeling classes and variables with meaningless names, or adding useless or meaningless code to an application binary are all possible steps in the process.
Obfuscation like this makes it impossible for hackers to evaluate the app’s code and comprehend how its algorithms function, much alone decrypt or recreate a created software code.
Artificial Intelligence
Currently, bank revenues in several countries exceed national income. As a result, they are among the first financial institutions to adopt Artificial Intelligence. AI assists in the analysis of client habits. Banks may customise their client communication, advise, services, and AI-enabled payments.
AI is useful in combating cybercrime, money laundering, and financial fraud. As a result, it not only enables the automation of high-value complex operations, speedier transactions, and customer comfort, but it also detects compromised data and data breaches, ensuring client privacy and security.
Conclusion
As you can see, FinTech is plagued by various fintech industry challenges. Data privacy will continue to be major concerns when it comes to FinTech apps. Security and consumer data security should be prioritized in security best practices for FinTech application development; failing to do so can be dangerous. Data breaches and leaks can potentially affect a company’s data.
We provide senior technical expertise and product development services to create high-quality software, including complicated but reliable FinTech solutions.
We can create a software platform from scratch or assist you in improving an existing product at a reasonable price. If you need to recruit remote developers for your projects, EVNE Developers team is here to help you.